Is Kraken Safe to Use? A Look at Its Security Features
TL;DR: Yes, among centralized exchanges, Kraken is widely regarded as one of the safer options thanks to long-running operational security, rigorous audits, and strong user-side protections.
If you’re weighing up where to deposit your first (or next) chunk of crypto, “how safe is Kraken?” will be near the top of your list and rightly so.
Exchange risk is a combination of what the platform protects against and what you protect against. Our goal here is to separate marketing from mechanics and walk through Kraken’s security stack in plain English.
Throughout this guide, we’ll show you what Kraken security covers, what it can’t, and how to harden your setup in minutes.
Quick Takeaways: Kraken's Security Overview
13 years, zero hacks: Kraken has operated since 2011 without a single breach resulting in customer fund losses.
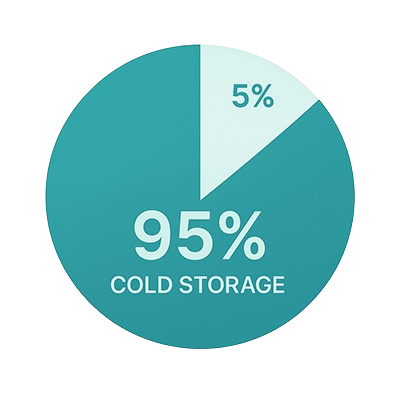
95% cold storage: Nearly all customer crypto sits offline in air-gapped, multi-signature vaults that hackers can't touch.
Quarterly proof-of-reserves: Independent audits verify Kraken holds 100%+ of customer assets, and you can verify your own balance.
Hardware keys and lockdowns: From YubiKey 2FA to 72-hour settings locks, Kraken gives you institutional-grade account protection.
Kraken's Security Track Record
When an exchange celebrates its 14th birthday without losing customer funds, that's not luck, it's institutional discipline.
Kraken launched in 2011, less than two years after Bitcoin itself. Back then, the playbook for securing digital assets didn't exist. Mt. Gox was still the dominant exchange. The infrastructure was experimental. And most platforms treated security as an afterthought until it was too late.
Kraken took a different path.
While competitors scrambled to build features, Kraken spent its early years building security infrastructure. That decision paid off during the 2013-2014 exchange crisis. Mt. Gox collapsed with 850,000 Bitcoin gone. Smaller exchanges folded weekly. But Kraken survived and eventually helped facilitate the Mt. Gox bankruptcy claims process.
The pattern continued. When Bitfinex lost $72 million in 2016, Kraken remained secure. When Coincheck hemorrhaged $534 million in 2018, Kraken's cold storage held firm. During the 2022 exchange contagion that followed FTX's collapse, Kraken published proof-of-reserves while others went dark.
The numbers speak clearly:
14+ years of continuous operation
Zero major platform breaches affecting customer funds
Over $21.5 billion in verified customer assets (November 2024 audit)
Quarterly proof-of-reserves since 2022 (pioneered the practice in 2014)
Kraken has also earned external recognition for its security practices. The platform holds ISO/IEC 27001:2013 certification, which is the international gold standard for information security management. It's completed SOC 2 Type 1 examinations, demonstrating compliance with strict security controls.
In July 2024, Kraken co-founded the Blockchain Security Standards Council alongside Coinbase, Anchorage Digital, and other major players. The goal: establish voluntary security standards across the industry. When an exchange helps write the rulebook, that signals maturity.
The June 2024 Security Incident: What Actually Happened
In June 2024, Kraken experienced what it described as a security incident, although not in the way most people imagine an exchange hack. A security researcher discovered a zero-day vulnerability in Kraken's funding system and reported it through the bug bounty program. So far, textbook responsible disclosure.
Then things went sideways.
According to Kraken's Chief Security Officer Nick Percoco, the researcher shared the vulnerability with two associates, who exploited it to withdraw nearly $3 million from Kraken's treasury, not customer funds. When Kraken requested technical details and the return of the funds, the individuals refused and demanded a meeting with Kraken's business team before returning the money.
Kraken called this extortion, not ethical hacking. The blockchain security firm CertiK later revealed it had discovered the vulnerabilities.
Key facts about the incident:
No customer assets were affected or at risk
Kraken identified and patched the vulnerability within 47 minutes
The exploit targeted company funds, not user balances
The individuals refused to follow standard responsible disclosure practices
This incident is instructive for two reasons. First, it demonstrates Kraken's rapid response capability in identifying and fixing a critical bug in under an hour. Second, it shows the difference between platform security (which held firm) and novel attack vectors (which require constant vigilance).
Contrast this with actual exchange breaches: Binance's 2019 loss of $40 million in customer Bitcoin, or the 2022 BNB Chain hack that drained $570 million. Those were catastrophic failures of custody. Kraken's incident was a treasury-level exploit that affected zero customers.
What the Track Record Tells Us
A clean 14-year security record suggests several things about Kraken's operational culture:
Proactive security posture. Kraken doesn't wait for breaches to invest in protection. It employs a dedicated security team led by industry veterans, runs an active bug bounty program (over $100,000 paid to researchers), and conducts regular penetration testing. These aren't reactive measures - they're baseline expectations.
Systemic risk management. Surviving multiple crypto winters, regulatory crackdowns, and market crashes requires more than good technology. It requires sound governance, healthy banking relationships, and conservative risk management. Kraken's proof-of-reserves program, licensing across multiple jurisdictions, and transparent operations all point to institutional maturity.
No complacency. The June 2024 incident demonstrates that even well-secured platforms are vulnerable to evolving threats. What matters is response time and the limitation of impact. Kraken's 47-minute fix and zero customer impact demonstrate preparedness, not invulnerability.
The trust equation. In crypto, longevity breeds legitimacy. Platforms that survive for this many years do so because they prioritize long-term reputation over short-term profit. Kraken's conservative approach, characterized by slow feature rollouts, rigorous compliance, and transparent audits, reflects this priority.
Of course, past performance doesn't guarantee future safety. The crypto graveyard is full of exchanges that were "secure" until they weren't. But a 14-year track record with zero customer fund losses is as close to proof as this industry offers.
But safety extends beyond platform security. It's about the architecture protecting your funds, which is where cold storage enters the picture.
Cold Storage & Asset Protection
The 95% Cold Storage Model
Here's the fundamental security question for any exchange: when hackers inevitably target your platform, can they actually reach customer funds?
For Kraken, the answer is mostly no, and the "mostly" matters.
Kraken’s defense strategy is a cold-first approach. Over 95% of customer deposits are held in cold storage. That means no network connection, no remote access, no attack surface for hackers to exploit. These are air-gapped systems physically isolated in secure facilities, not just offline computers.
The remaining 5% sits in hot wallets, which are internet-connected systems that handle day-to-day operations like withdrawals and trading. This is the liquidity layer that makes Kraken functional.
Why the split matters:
When you hear about exchange hacks such as Binance's $40 million loss, or Coincheck's $534 million disaster, you're almost always hearing about hot wallet compromises. Hackers break into internet-connected systems and drain whatever they can reach.
With 95% in cold storage, Kraken limits the damage. Even if attackers breached the hot wallet infrastructure (which hasn't happened), they'd only access 5% of funds. The bulk stays locked in vaults they can't touch.
Cold Storage Security Architecture
Cold storage sounds simple: "just keep it offline." But it involves multiple overlapping security layers.
Storage Type | % of Assets | Primary Threats Protected Against | Access Requirements |
Cold Storage | 95% | Remote hacking, malware, phishing attacks, unauthorized access, network intrusions | Multi-signature approval, HSM key access, biometric authentication, physical vault entry, geographic coordination across facilities |
Hot Wallets | 5% | Excessive withdrawals, velocity attacks, unauthorized transactions | Automated monitoring systems, withdrawal velocity limits, rate caps, real-time anomaly detection |
Multi-signature wallets. Moving funds requires multiple authorized signatures from different team members. No individual, be it employee, contractor, or compromised account, can unilaterally access the vaults. You'd need to compromise multiple people simultaneously.
Hardware security modules (HSMs). These specialized devices generate and protect cryptographic keys. They're tamper-resistant, meaning attempts to physically open them destroy the keys inside. Even if someone gained physical access to a facility, they couldn't extract the keys needed to move funds.
Geographic distribution. Funds are spread across multiple secure facilities worldwide. This protects against localized risks, including natural disasters, regional conflicts, and facility-specific breaches. If one location goes offline, the majority of assets remain secure elsewhere.
Physical security. These facilities feature 24/7 armed surveillance, biometric access controls, video monitoring, and alarm systems. Multiple barriers exist between the outside world and the devices holding customer crypto.
Separation of duties. No single person at Kraken has complete access. Key generation happens separately from key storage. Vault access requires different credentials from transaction signing. Compromising one element doesn't compromise the entire system.
Regular audits. Independent auditors periodically verify that Kraken's cold storage holdings match what they claim. More on this in the Proof of Reserves section.
Hot Wallet Protection
That 5% in hot wallets provides the liquidity that makes instant withdrawals possible. But it's also the most exposed part of the system.
How Kraken secures it:
Automated monitoring tracks hot wallet activity in real-time, flagging unusual patterns. If withdrawal requests suddenly spike or target unexpected addresses, the system notices.
Withdrawal velocity controls limit how much can move in a given timeframe. Even if an attacker somehow compromised a hot wallet, they can't drain it instantly. Rate limits and daily caps provide circuit breakers.
Insurance coverage protects hot wallet holdings through Lloyd's of London and other underwriters. If a breach occurred, insurance would cover customer losses – though Kraken's excellent track record suggests they haven't needed to file a claim.
Proof-of-Reserves
Since 2014, Kraken has published proof-of-reserves audits that cryptographically demonstrate they hold customer assets. This isn't a practice born from FTX's collapse – Kraken pioneered it over a decade ago. But the cadence has accelerated. In 2025, Kraken began publishing these audits quarterly, rather than semiannually.
What it actually verifies:
An independent accounting firm takes a snapshot of all customer balances at a specific point in time. They aggregate these balances into a Merkle tree - a cryptographic data structure that represents the total liabilities Kraken owes customers.
Simultaneously, the auditor verifies that Kraken controls wallet addresses holding those assets on-chain. They confirm Kraken can sign transactions from those addresses, proving ownership.
The result: cryptographic proof that Kraken holds 100%+ of customer assets. The September 2025 audit showed a 114.9% Bitcoin reserve ratio - Kraken held nearly 15% more Bitcoin than it owed customers.
Assets covered:
Bitcoin (BTC)
Ethereum (ETH)
Solana (SOL)
USD Coin (USDC)
Tether (USDT)
Ripple (XRP)
Cardano (ADA) - added March 2025
The audit includes spot holdings, margin positions, futures balances, and staked assets. Your actual exposure - not just your spot wallet - is verified.
You can verify your own holdings:
Kraken provides every customer with a Merkle proof showing their specific balance was included in the audit snapshot. You can download this proof and mathematically confirm your funds were counted.
You don't have to trust Kraken's word. You don't even have to trust the auditor. You can independently verify the cryptographic proof.
The limitations:
Proof-of-reserves confirms Kraken holds the assets at a specific moment. It doesn't reveal whether Kraken has undisclosed liabilities, whether assets are encumbered by loans, or Kraken's overall financial health beyond this specific asset category.
It's a snapshot, not a complete financial audit. But it's far more than most exchanges provide.
How this compares:
Many platforms claim to be "fully reserved" without offering verifiable proof. Some individuals publish wallet addresses without verifying that they control them. Others show assets without disclosing liabilities.
Kraken's approach - regular third-party audits with user-verifiable Merkle proofs and disclosed reserve ratios exceeding 100% - sets a standard few competitors meet. Coinbase doesn't offer comparable proof-of-reserves. Binance has published some attestations, but the methodology and frequency differ.
Crypto history is littered with platforms that promised full reserves right up until they collapsed. FTX claimed customer funds were safe. Celsius insisted deposits were secure. BlockFi maintained they were well-capitalized.
Kraken gives you the tools to verify rather than just believe.
Infrastructure and Platform Security
Technical Security Measures
Where assets are stored matters. So does the entire technology stack defending against intrusion.
Encryption. All sensitive data is encrypted both in transit and at rest. When data moves between your browser and Kraken's servers, SSL/TLS encryption protects it.
Database security. Access is strictly controlled based on role and necessity. Database activity is logged and monitored. Unusual queries trigger alerts. This limits insider threats - the risk that a rogue employee could exfiltrate customer data.
DDoS protection. Distributed denial-of-service attacks are constant threats. Kraken employs enterprise-grade mitigation that filters malicious traffic while allowing legitimate users through. The platform has weathered DDoS attacks without significant downtime.
Network segmentation. Kraken's infrastructure operates in isolated segments. Trading systems are separate from custody systems. Hot wallets are isolated from cold storage. A breach in one area doesn't cascade across the platform.
Server hardening. Every server is hardened with unnecessary services disabled, security patches applied promptly, and configurations following strict baselines. This reduces the attack surface.
Penetration testing. Kraken doesn't wait for hackers to find weaknesses. The platform conducts regular penetration tests where security experts attempt to break in. Automated vulnerability scanners continuously probe for security holes.
Operational Security Practices
Technology gets you part of the way. Security also depends on the humans operating the systems.
Employee vetting and training. Everyone at Kraken undergoes security training and background checks. Employees learn to recognize phishing, social engineering, and best practices in operational security.
Principle of least privilege. Employees only get access to systems they need for their job. Engineers working on trading features don't have access to cold storage systems. Customer support can view account details, but can't move funds.
Activity logging and monitoring. Every action generates logs: who accessed what, when, and why. These logs are monitored in real-time for suspicious patterns, such as unusual login locations or off-hours database access.
Incident response protocols. Kraken maintains detailed procedures for when incidents occur: who gets notified, how systems get isolated, and how customers get informed.
Third-party partnerships. Kraken partners with specialized security vendors for threat intelligence, monitoring, and defensive tools. These partnerships provide early warning about emerging threats.
Compliance with frameworks. Kraken adheres to ISO/IEC 27001:2013 and has completed SOC 2 Type 1 examinations. These represent ongoing compliance with rigorous security standards verified by independent auditors.
Software Development Security
Most security breaches originate from preventable bugs in code, rather than sophisticated exploits.
Secure code reviews. Before code goes into production, multiple engineers review it for security issues. This catches common mistakes - SQL injection vulnerabilities, authentication bypasses, and input validation errors.
Automated security testing. Kraken runs automated security scans on every code commit. Static analysis examines source code for vulnerabilities. Dynamic analysis tests running applications. These automated checks catch issues early when they're cheapest to fix.
Bug bounty program. Kraken pays security researchers to find and report vulnerabilities. The program has paid out hundreds of thousands of dollars to researchers who responsibly disclosed issues.
This crowdsources security expertise beyond Kraken's internal team, though the June 2024 incident showed that not all participants follow responsible disclosure.
Rapid patching. When security issues are discovered, Kraken follows a structured process: triage severity, develop a fix, test thoroughly, deploy, and notify affected users if necessary.
Supply chain security. Modern software relies on open-source libraries and third-party dependencies. Kraken monitors these components for known vulnerabilities and updates them promptly. This prevents supply chain attacks where compromised dependencies introduce vulnerabilities.
Regulatory Compliance and Licensing
Regulation adds another layer of security accountability.
Licenses held. Kraken operates under multiple regulatory licenses worldwide. In the US, it's registered with FinCEN as a Money Services Business and holds state-level Money Transmitter Licenses. Internationally, Kraken maintains licenses in the UK, Canada, Australia, and other jurisdictions.
KYC and AML programs. Regulatory requirements mandate that Kraken verify customer identities and monitor for suspicious activity. While these programs primarily target financial crime, they also create audit trails that improve security.
Regulatory oversight. When regulators examine Kraken's operations, they review security controls, custody practices, and incident response capabilities. This external scrutiny creates accountability beyond what customers can verify themselves.
Why regulation helps. Unlicensed, offshore exchanges can operate without oversight, cutting corners on security to maximize profit. Licensed exchanges face regular examinations and must demonstrate compliance with security standards.
The March 2025 dismissal of the SEC lawsuit (with prejudice, meaning it can't be brought again) removed regulatory uncertainty while maintaining Kraken's licensed, compliant status.
In 2024, Kraken received 6,826 data requests from law enforcement and regulatory agencies across 71 countries. The platform published a transparency report detailing these requests, highlighting their level of accountability.
User-Level Security Features
Exchange security is only half the equation. The rest depends on what you do once you log in. Kraken gives users one of the most comprehensive security toolkits in the industry, but it’s up to you to switch it all on. Here’s how to lock things down like a pro.
Two-Factor Authentication (2FA)
If you only do one thing today, make it this. 2FA adds a second verification step when you log in, trade, or withdraw.
Kraken supports multiple methods:
Authenticator app (recommended): Google Authenticator or Authy generate a rotating code that must match what Kraken expects.
Hardware security key: For the highest level of protection, devices like YubiKey or Titan Key use cryptographic authentication instead of codes that can be phished.
FIDO2/Passkeys: The latest method, allowing biometric logins on supported devices - fast and secure.
Kraken’s systems are designed to block SMS-based 2FA because it’s vulnerable to SIM-swapping. That’s an early sign they take account-level protection seriously.
Master Key
Think of this as your “emergency override.” It’s a separate code that can reset your password or 2FA if your main credentials are compromised. You should generate it, write it down, and store it offline (not on your phone or computer). If someone tries to take over your account, this is what gets it back under your control.
Global Settings Lock (GSL)
One of Kraken’s most underrated features. When enabled, GSL freezes all critical account settings - things like withdrawal addresses, API keys, and 2FA methods - until you manually disable the lock using your Master Key.
That means even if someone steals your login, they can’t silently change withdrawal settings or create a new API key to drain your funds.
Withdrawal Whitelisting
You can set up an approved list of wallet addresses for withdrawals. Once GSL is active, those addresses can’t be changed.
If an attacker tries to send your funds elsewhere, Kraken will simply block it. Combine this with time-delayed withdrawals, and you have extremely strong outbound protection.
API Key Controls
Traders using bots or third-party portfolio tools will appreciate Kraken’s granular API permissions.
Each key can be customized to allow (or deny) actions such as:
Viewing balances only
Trading without withdrawals
Managing open orders
You can also lock API access by IP address, which means only your server or app can use that key.
PGP-Signed and Encrypted Emails
Phishing remains one of crypto’s biggest threats. Kraken digitally signs all official emails with PGP so users can verify authenticity. For even stronger security, you can enable PGP email encryption for sensitive correspondence, ensuring that only you can read messages about your account.
Account Monitoring and Alerts
Kraken actively monitors for suspicious logins or changes and will send real-time alerts for new device sign-ins, withdrawals, or password resets.
If anything looks off, GSL and Master Key protection stop the attacker cold, but it’s still smart to act fast.
How Kraken Stacks Up Against Competitors
Security-wise, Kraken holds its own against the big names, but each exchange brings something different to the table.
Kraken vs. Coinbase
Both are US-regulated and compliance-focused. Coinbase has the advantage of being publicly traded (more regulatory scrutiny) and offers FDIC insurance on USD balances.
But here's where Kraken pulls ahead: those quarterly proof-of-reserves audits with verifiable Merkle proofs. Coinbase doesn't offer anything comparable, so you're taking their word on asset backing.
If you want the full feature breakdown, we've got a complete Kraken vs. Coinbase comparison.
Kraken vs. Binance
Binance wins on fees and variety - more coins, lower costs, bigger liquidity. But the security track record? Not even close. Binance lost $40 million in customer Bitcoin (2019) and took a $570 million hit in the BNB Chain hack (2022). Kraken? Zero customer fund losses from breaches.
Binance has its SAFU insurance fund, but Kraken's cold storage model and transparent reserves feel more bulletproof.
Bottom line: pick based on what matters most - verified reserves and regulatory clarity (Kraken), ease of use for beginners (Coinbase), or maximum trading flexibility (Binance).
What Kraken Cannot Protect Against
Kraken's security is solid, but it has limits. Understanding what the platform can't protect you from matters just as much as knowing what it can.
User-Side Security Failures
Kraken can build the most sophisticated security infrastructure on the planet, but if you reuse passwords from a breached database, use SMS-only 2FA, or fall for a phishing email, none of it matters.
The most common ways people lose funds have nothing to do with exchange vulnerabilities. They click a link in a fake "urgent security alert" email and hand over their credentials.
They use the same password across ten different sites. They skip 2FA entirely or stick with SMS codes that can be intercepted through SIM-swapping.
Kraken gives you hardware key support, Global Settings Lock, Master Key protection, and withdrawal whitelisting. These tools only work if you actually enable them.
Custodial Risk: The Trade-off You're Making
Here's the fundamental issue with any centralized exchange: you don't control your private keys. Kraken does.
When you deposit crypto to Kraken, you're trusting them to hold it safely. Their cold storage, multi-signature wallets, and proof-of-reserves mitigate this risk to a fair degree. But trust is still required.
Compare this to a hardware wallet you control. With self-custody, no company bankruptcy, government seizure, or policy change can touch your funds. The trade-off? You're responsible for everything – lose your seed phrase, and your crypto is gone forever.
Threats Beyond Kraken's Control
Regulatory risk: Governments can seize exchange assets, freeze accounts, or force platforms to exit jurisdictions. Kraken maintains strong compliance, but regulatory landscapes shift.
Physical coercion: If someone threatens you with violence to access your account, Kraken's security features won't help.
Sophisticated social engineering: Attackers might target you directly, calling and pretending to be Kraken support. Kraken will never call asking for passwords or 2FA codes.
Network-level attacks: BGP hijacking and DNS poisoning can redirect you to fake Kraken sites. Always verify URLs manually.
Managing Exchange Risk
No exchange can guarantee 100% safety. Kraken's 14-year track record, transparent reserves, and security-first culture put it in a different category from platforms that have failed. But custodial services mean inherent risk remains.
Best practice: Use Kraken for what exchanges do well - trading, liquidity, fiat on/off ramps. For long-term holdings you're not actively trading, move them to a hardware wallet. That's not a knock on Kraken. That's just smart crypto security.
Security Checklist: Lock Down Your Kraken Account
☐ Enable hardware key 2FA (YubiKey or similar)
☐ Generate and store Master Key offline (write it down, keep it safe)
☐ Activate Global Settings Lock
☐ Set up withdrawal address whitelisting
☐ Restrict API keys by IP address and permissions
☐ Enable PGP-signed email notifications
☐ Review login history weekly
☐ Use a unique, strong password (20+ characters)
☐ Transfer long-term holdings to a hardware wallet
☐ Bookmark official Kraken URL (never click email links)
Final Assessment: Is Kraken Safe?
So, is Kraken safe to use?
Among centralized exchanges, yes - Kraken ranks as one of the safest options available.
But "safe" doesn't mean "risk-free."
Kraken can't protect you from your own security mistakes. It can't eliminate the inherent risks of custodial services. And it can't guarantee immunity from regulatory actions or unforeseen threats.
The honest answer: Kraken provides strong platform security and gives you powerful tools to secure your account. Whether your funds stay safe depends on how you use those tools and how much you're willing to trust a third party with custody.
For active trading, Kraken offers one of the most secure environments in crypto. For long-term holdings, a hardware wallet with your keys beats any exchange - Kraken included.
Security in crypto is a spectrum, not a binary. Kraken sits at the reliable end of that spectrum, but the safest approach combines exchange use for trading with self-custody for storage.
Choosing a secure exchange is important, but so is everything that comes after.
LearningCrypto gives you AI-driven insights, portfolio management tools, and real-time analytics to help you protect and grow your investments.
Get started with LearningCrypto →
Frequently Asked Questions
Does Kraken offer insurance on my crypto?
Kraken maintains insurance coverage through Lloyd's of London for assets in hot wallet storage (the 5% online). This covers platform-level breaches, not individual account compromises from phishing or stolen passwords.
Can Kraken freeze or seize my account?
Yes, under certain circumstances. Kraken complies with legal requirements and can freeze accounts in response to law enforcement requests, court orders, or suspected violations of terms of service. In 2024, Kraken received 6,826 data requests from agencies across 71 countries. This is standard for regulated exchanges - the trade-off for operating legally and maintaining banking relationships.
How do I verify Kraken actually holds my crypto?
Log in to your account and access the Proof of Reserves portal. Download your Merkle proof, which shows your balance was included in the most recent audit snapshot. You can verify this cryptographically without trusting Kraken's word. The latest audits cover BTC, ETH, SOL, USDC, USDT, XRP, and ADA.
Disclaimer: This article is for educational purposes only and does not constitute financial advice. Cryptocurrency investments carry risk; you should always do your own research before making any investment decisions.